- Impact
- 267
Domainers Against Multi-Factor Authentication (MFA) Now = DAMN
Like, DAMN son, I find being forced to use MFA to login to a site multiple times per day to be ...
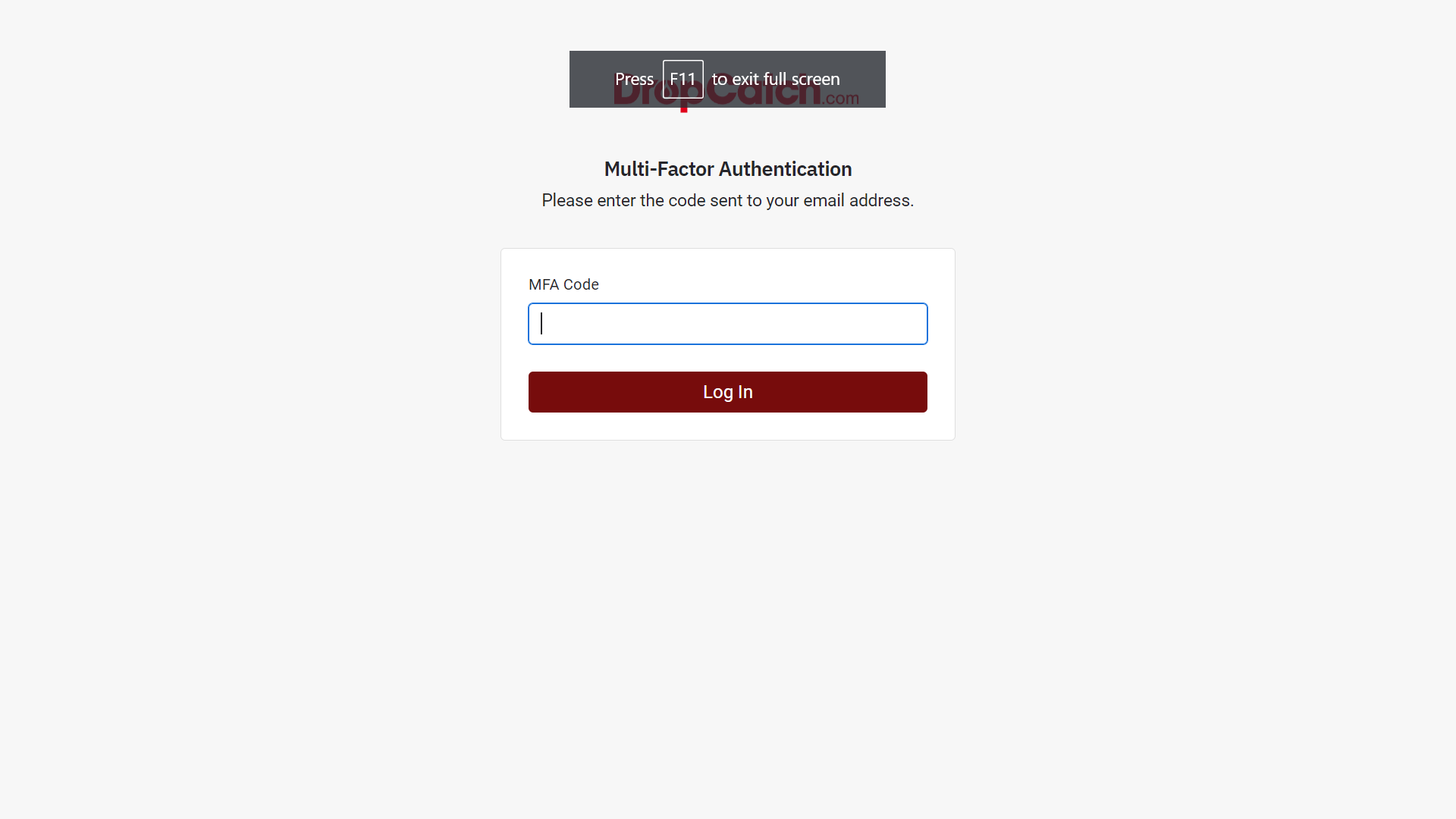
DropCatch as of this week has now instituted mandatory MFA, and according to a support rep will not allow it to be disabled on an individual level.
However if enough domainers speak out about this travesty and apply pressure we may be able to arrest this madness before it becomes normalized as has been happening lately across registrars, marketplaces and other domain related platforms alike.
If you add up the time lost for having to use MFA and 2FA every day, multiple times per day, across multiple sites, it is costing perhaps millions of dollars in lost work to the domainer community. Even if on average it takes a minimum extra 30 seconds to login (it's likely more) that is already over 3 hours of lost work in a year. Nearly a half day! If you do it twice/day over a year that's 6 hours, ... 5x per day = 15 hours lost!! Imagine losing near 2-days of work per year for something like this. It's mind boggling.
Yes, there is a case for using MFA at the registrar level to protect against theft of our valuable domain properties, but now this practice is bleeding over to other sites and platforms where it should be up to the individual (always) to swim at their own risk, and balance their choice with other factors such as time expenditure.
Can I get a Whoa Bundy!?
Like, DAMN son, I find being forced to use MFA to login to a site multiple times per day to be ...
- A waste of valuable, productive time
- Wholly unnecessary
- Generally insufferable
DropCatch as of this week has now instituted mandatory MFA, and according to a support rep will not allow it to be disabled on an individual level.
However if enough domainers speak out about this travesty and apply pressure we may be able to arrest this madness before it becomes normalized as has been happening lately across registrars, marketplaces and other domain related platforms alike.
If you add up the time lost for having to use MFA and 2FA every day, multiple times per day, across multiple sites, it is costing perhaps millions of dollars in lost work to the domainer community. Even if on average it takes a minimum extra 30 seconds to login (it's likely more) that is already over 3 hours of lost work in a year. Nearly a half day! If you do it twice/day over a year that's 6 hours, ... 5x per day = 15 hours lost!! Imagine losing near 2-days of work per year for something like this. It's mind boggling.
Yes, there is a case for using MFA at the registrar level to protect against theft of our valuable domain properties, but now this practice is bleeding over to other sites and platforms where it should be up to the individual (always) to swim at their own risk, and balance their choice with other factors such as time expenditure.
Can I get a Whoa Bundy!?
Last edited:






